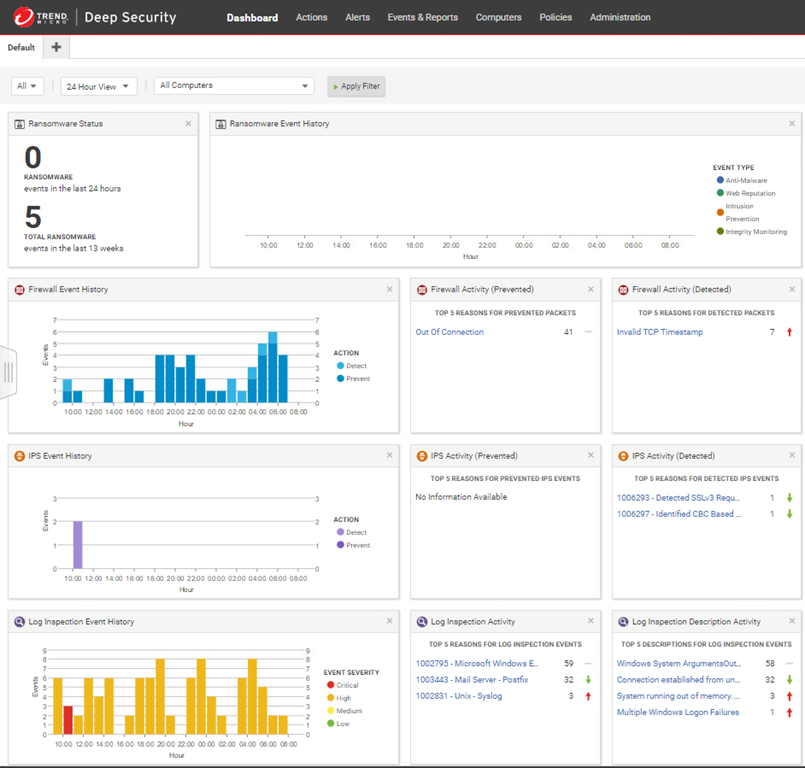
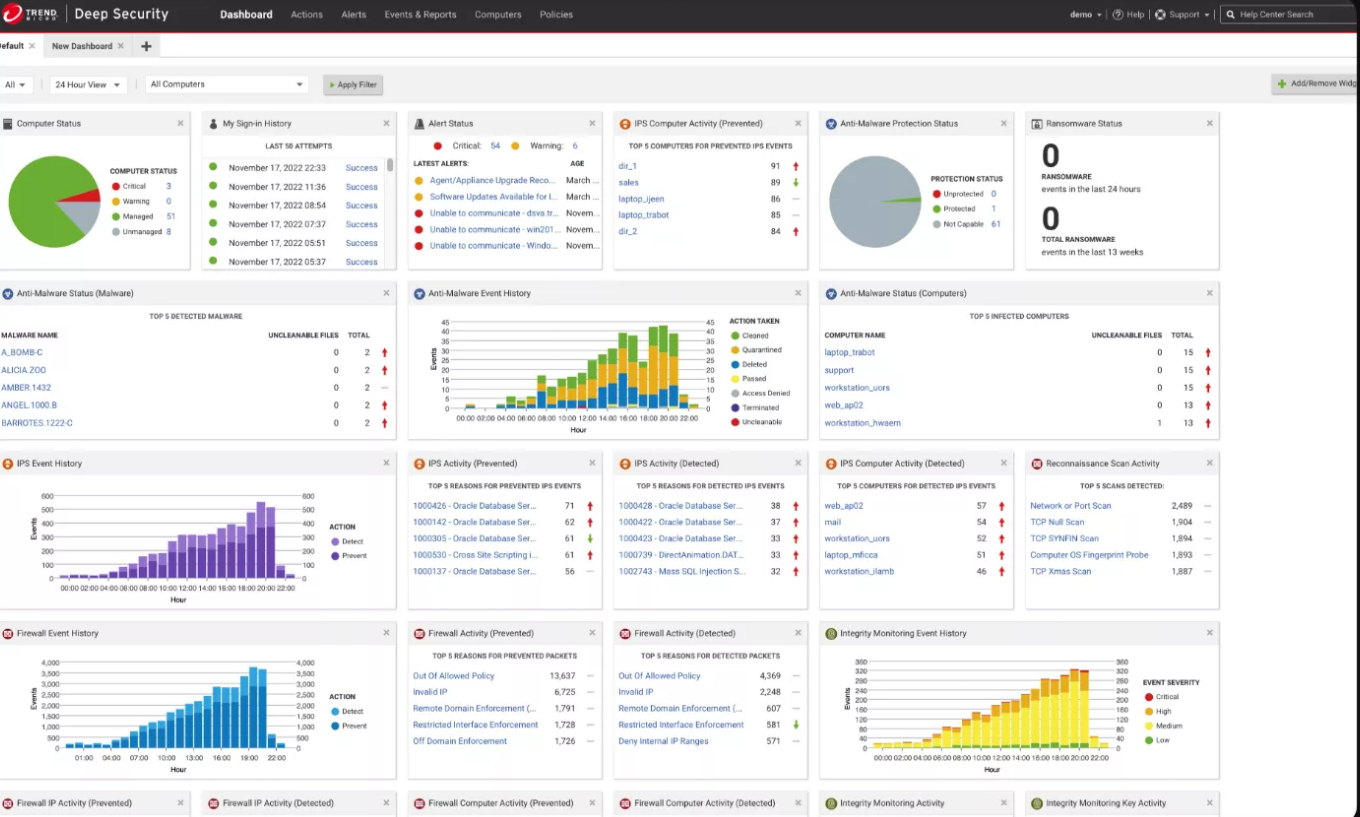
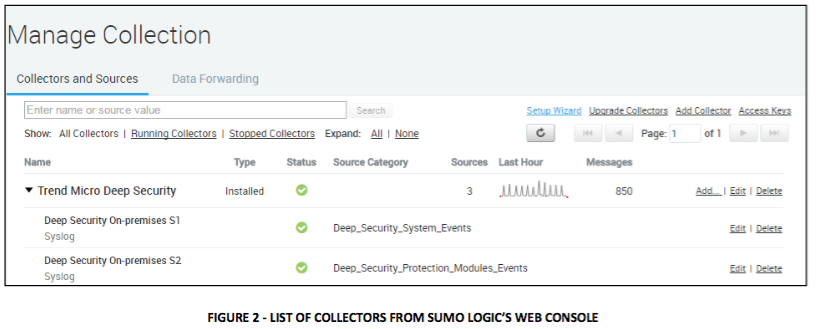
GitHub - deep-security/amazon-sns: Scripts to parse events from Trend Micro Deep Security via Amazon SNS.

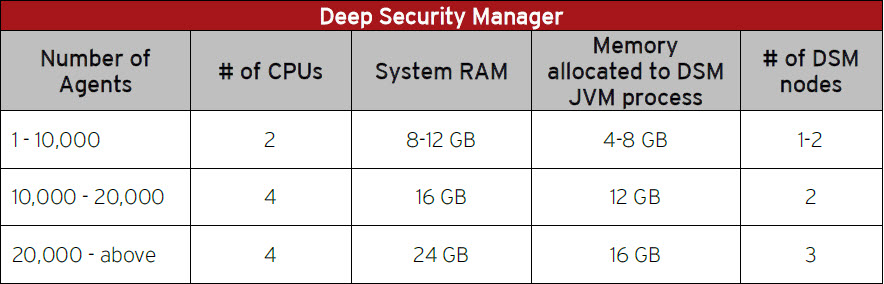
Trend Micro Deep Security 12 for Certified Professionals - eBook v1 - Protected 1 .pdf - Trend Micro™ Deep Security™ 12 Training for Certified | Course Hero